Securing Azure Functions and Logic Apps
🎯 TL;DR: Cost-Optimized Security for Serverless Microservices
Consumption plan Function Apps and APIM Standard lack VNet integration for cost optimization but expose services publicly. Problem: Serverless microservices accessible directly bypassing API Management security policies. Solution: IP restriction-based security using APIM’s public IP address to whitelist only API Management access, configuring both main site and SCM site restrictions. Architecture includes Azure Front Door for WAF capabilities since APIM Standard lacks native WAF protection.
Here is a scenario that I recently encountered. Imagine we are building micro-services using serverless (a mix on Azure Function Apps and Logic Apps) with APIM in the front. Lets say we went with the APIM standard instance and all the logic and function apps are going to be running on consumption plan (for cost reasons as its cheaper). This means we wont be getting any vnet capability and our function and logic apps will be exposed out to the world (remember to get vnet with APIM we have to go with the premium version, we are going APIM standard here for cost saving reasons).
So how do we restrict our function and logic apps to only go through the APIM, in another words all our function and logic apps must only go through the APIM and if anyone tries to access them directly they should be getting a “HTTP 403 Forbidden”.
Lets visualize this scenario; We have some WAF capable ingress endpoint, in this case its Azure Front Door, that is forwarding traffic to APIM which then sends the requests to the serverless apps.
Reason for having Front Door before APIM is because APIM doesn’t have WAF natively so we will need to put something in front of it that has that capability to be secure.
There are few options like Azure Firewall, Application Gateway etc, but for the purposes of this scenario we have Azure Front Door in front of APIM (and we can have an APIM policy that will only accept traffic from Azure Font Door, we wont be going in to that, we will keep it to securing our function apps to just being available via APIM for today)
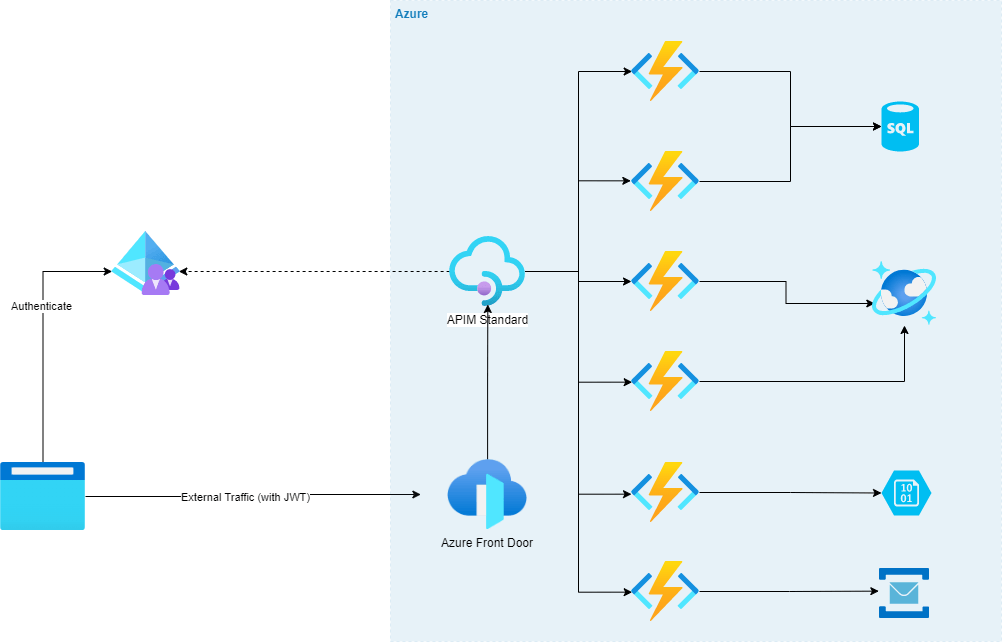
Securing the function app
- First we will need to get the public ip address of the APIM
- White-list this address in our function app network restrictions
Getting the public ip of APIM
You can go to the APIM resource in the Azure portal and get it from there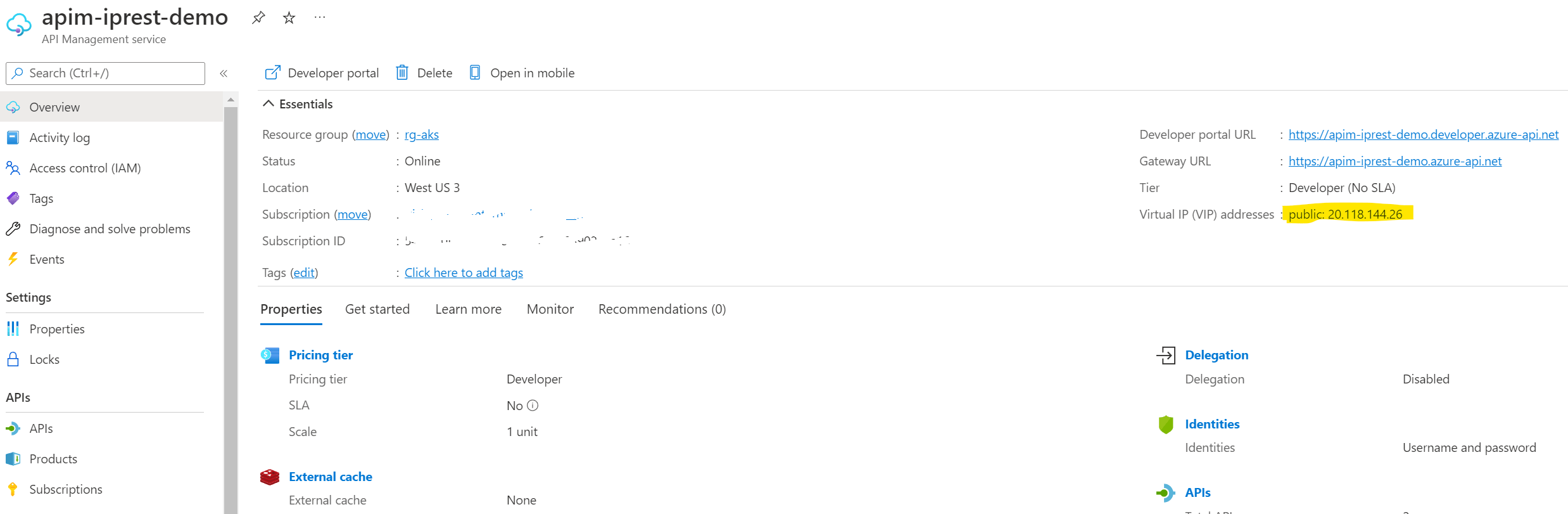
Or you can use the CLI and run
1 | az apim show --name "apim-name" --resource-group "resource-group-name" |
White-listing the function app
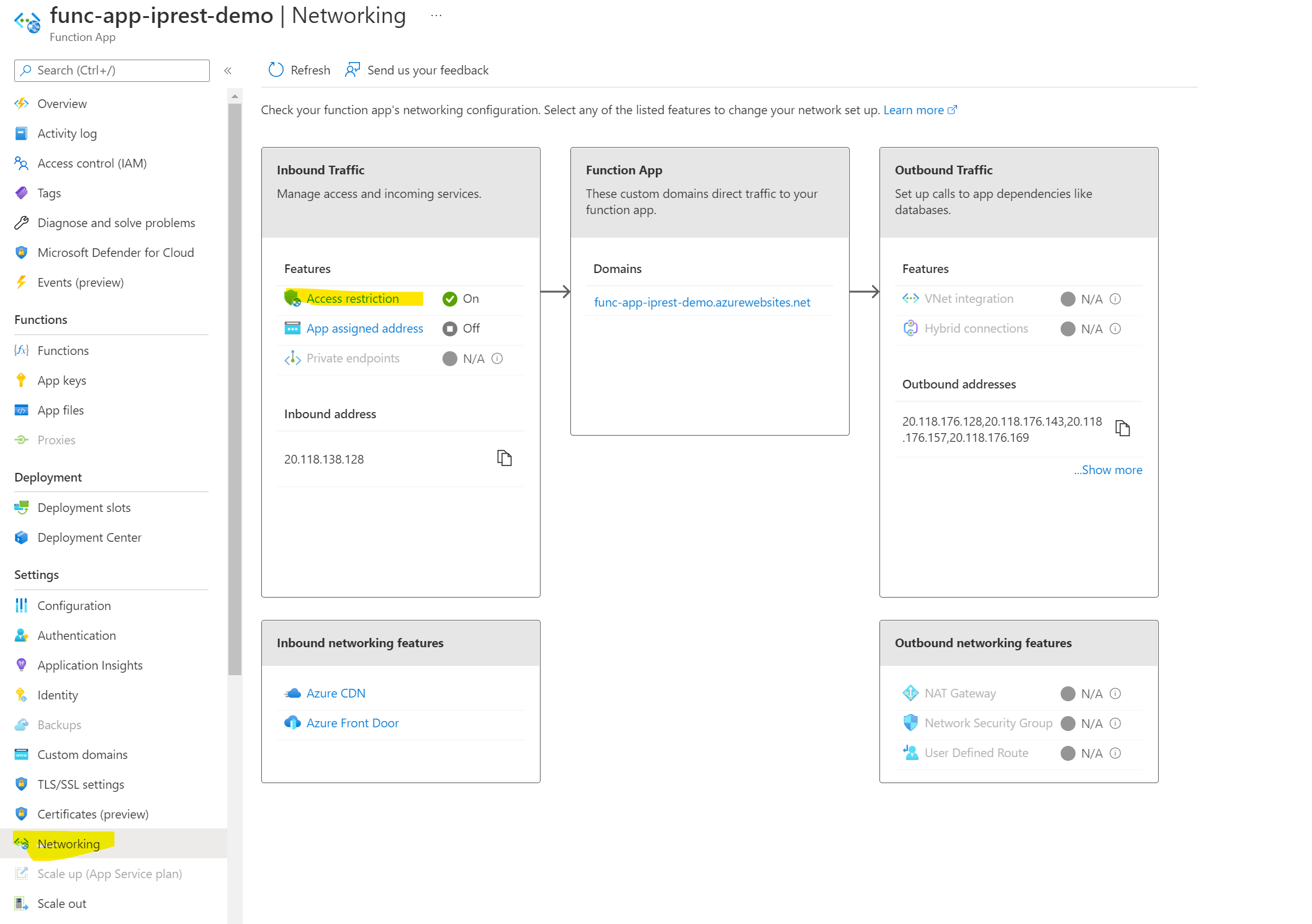
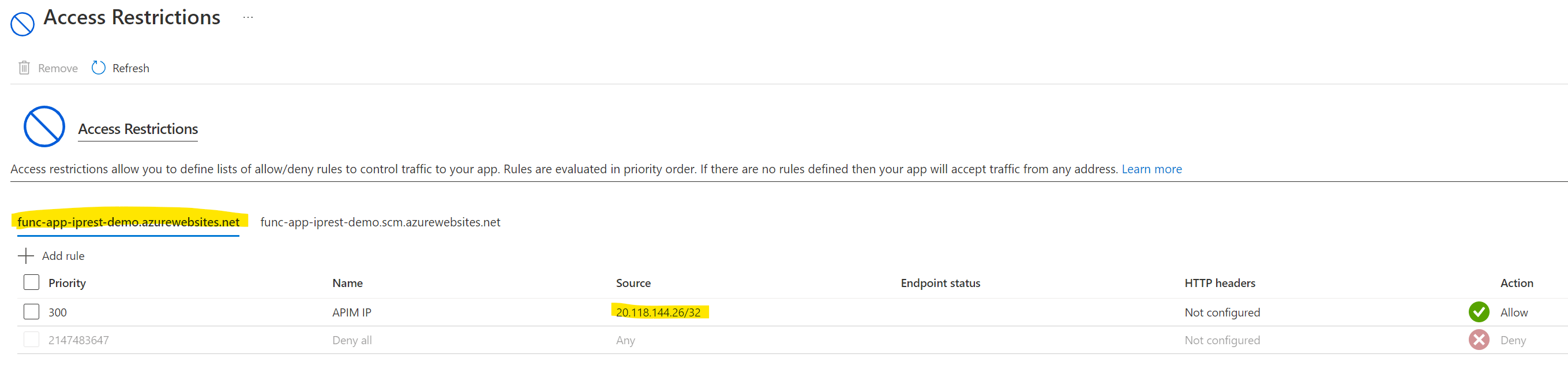
- You need to go into networking -> access restriction
- Only allow the APIM ip (once you enter this, the deny all will automatically come ie: all other ip’s are denied)
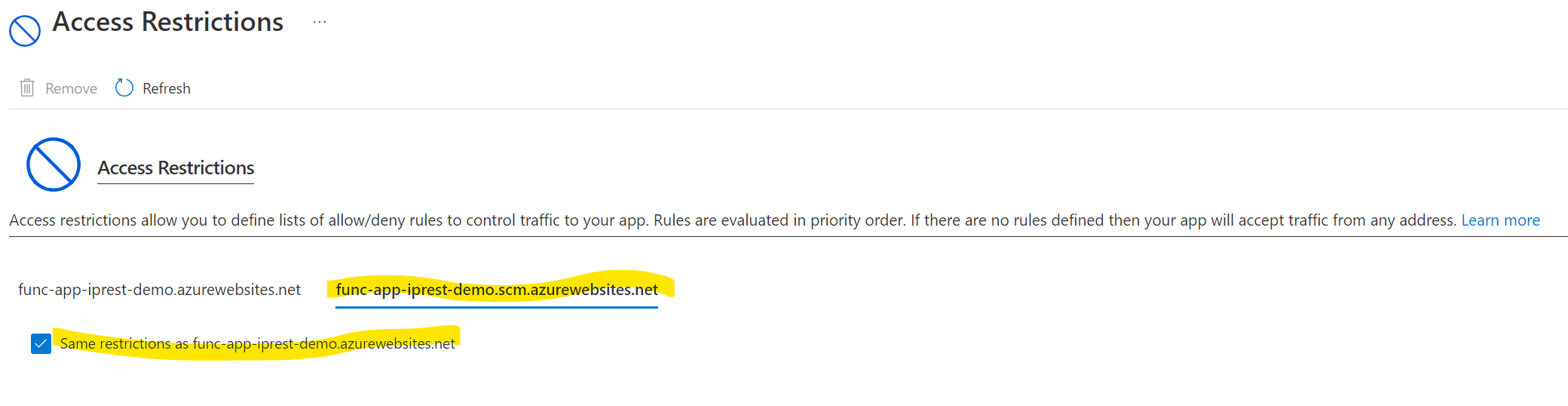
- Its important that the SCM site is also blocked. More about Kudu service that powers the SCM site here
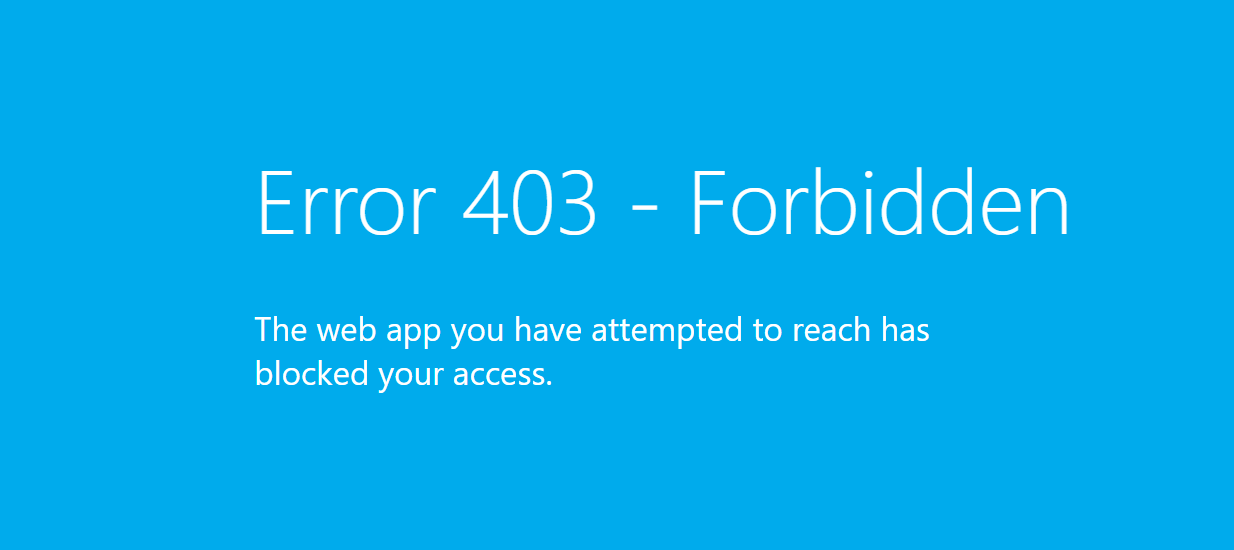
What happens if you try to access this function
Now its all blocked we get a nice HTTP 403 Forbidden
What about deploying code to this function via GitHub Actions
When you try to deploy to these functions using GitHub Actions or even via Azure Devops you will get the same HTTP 403 and wont be able to deploy. This is because the GitHub runner’s ip address will be blocked; remember we are only allowing APIM in, all others are blocked.
There are a couple of ways to get around this. I talk about this in the next post, you can check it out here
References
- Cover image has been taken from https://azure.microsoft.com/en-us/services/functions/#overview
Securing Azure Functions and Logic Apps
https://clouddev.blog/Azure/Function-Apps/Security/securing-azure-functions-and-logic-apps/